- Home
- NOC & SOC Operations
NOC & SOC Operations
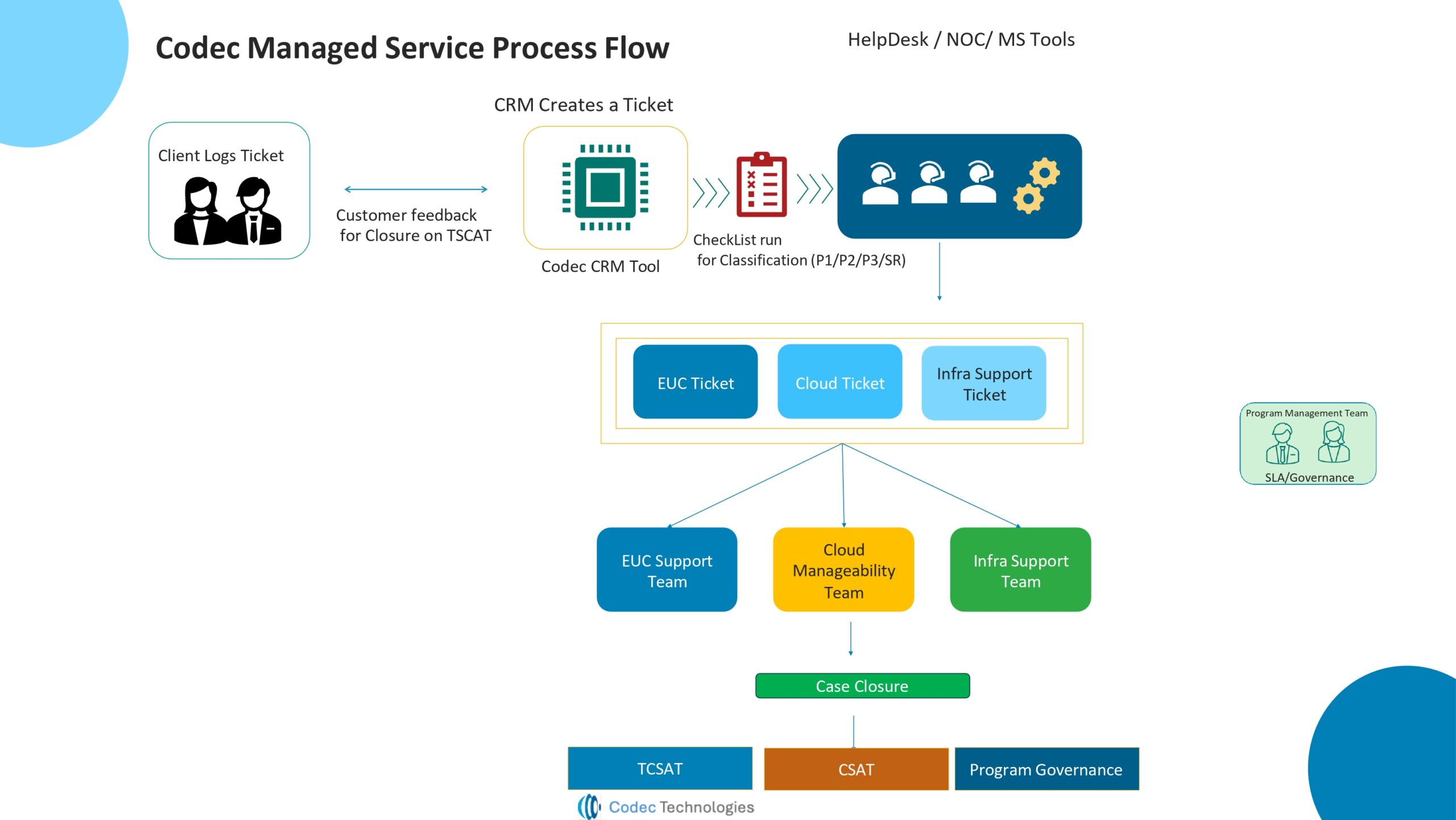
In the rapidly evolving IT landscape, maintaining security and operational efficiency is paramount for organizations. Two critical components that play a vital role in achieving these objectives are Network Operations Centers (NOC) and Security Operations Centers (SOC). While both are integral to the IT industry, they serve distinct functions that are essential for the smooth and secure operation of IT systems. This article delves into the roles, functions, and differences between NOCs and SOCs, highlighting their importance in modern organizations.
What is a Network Operations Center (NOC)?
A Network Operations Center (NOC) is a centralized location where IT professionals monitor, manage, and maintain an organization’s network infrastructure. The primary goal of a NOC is to ensure the availability, performance, and reliability of network services. NOCs are typically staffed with network engineers and technicians who work round-the-clock to respond to incidents, troubleshoot issues, and optimize network performance.
The Importance of NOC and SOC in Modern Organizations
- 1. Enhanced Security Posture: With dedicated teams focused on network performance and security, organizations can better protect their assets from cyber threats.
- 2. Improved Operational Efficiency: Continuous monitoring and proactive management of network infrastructure lead to reduced downtime and improved service delivery.
- 3. Faster Incident Response: The collaboration between NOC and SOC teams enables organizations to respond swiftly to incidents, minimizing potential damage and recovery time.
- 4. Regulatory Compliance: By maintaining robust security measures and operational oversight, organizations can ensure they meet industry regulations and standards.
Key Functions of a NOC:
1. Monitoring and Incident Management: NOC teams continuously monitor network traffic, performance, and health. They use advanced tools to identify and resolve issues before they escalate into major problems.
2. Network Maintenance: NOCs perform regular maintenance tasks, such as software updates, hardware upgrades, and configuration changes, to ensure optimal network performance.
3. Performance Optimization: By analyzing network data, NOC teams can identify bottlenecks and inefficiencies, implementing solutions to enhance overall network performance.
4. Communication and Coordination: NOCs serve as the main point of contact for incident reporting and resolution. They coordinate with other IT teams to ensure effective communication during incidents.
What is a Security Operations Center (SOC)?
A Security Operations Center (SOC) is a dedicated facility that focuses on monitoring and protecting an organization’s information systems and data from security threats. SOC teams are responsible for identifying, analyzing, and responding to cybersecurity incidents in real-time. They employ various security tools and techniques to defend against potential threats and ensure compliance with security policies and regulations.
Key Functions of a SOC:
1. Threat Detection and Response: SOC teams continuously monitor security alerts and logs to detect potential threats. They analyze incidents to determine their severity and respond promptly to mitigate risks.
2. Incident Management: When a security incident occurs, the SOC leads the investigation, containment, and recovery efforts. They document incidents for future reference and improvement.
3. Vulnerability Management: SOC teams regularly conduct vulnerability assessments and penetration testing to identify and remediate weaknesses in the organization’s security posture.
4. Compliance and Reporting: SOCs ensure that the organization adheres to relevant security regulations and standards. They generate reports for compliance audits and management reviews.
Key Differences Between NOC and SOC:
While both NOCs and SOCs are crucial for maintaining the integrity of IT operations, they differ in their focus and functions:
– Focus: NOCs primarily concentrate on network performance and reliability, while SOCs are dedicated to cybersecurity and threat management.
– Skill Sets: NOC teams often consist of network engineers and technicians with expertise in network management, whereas SOC teams are made up of cybersecurity analysts and specialists with knowledge of information security.
– Tools and Technologies: NOCs utilize network monitoring tools and performance management systems, while SOCs rely on security information and event management (SIEM) systems, intrusion detection systems (IDS), and other security tools.
Summary
NOCs and SOCs are essential components of modern IT operations, each serving unique yet complementary roles. By understanding their functions and importance, organizations can better allocate resources and strategies to enhance both network performance and security. As the IT landscape continues to evolve, investing in effective NOC and SOC capabilities will be crucial for organizations aiming to thrive in an increasingly complex and threat-prone environment.


